As businesses become increasingly reliant on technology, they are also becoming more vulnerable to cyber-attacks.
A cyber-attack can be a devastating event for a business, resulting in the loss of valuable data and impact on a company’s reputation and bottom line.
Each quarter, CERT NZ releases a report of what has occurred across the NZ Business Community.
Here are a few of the latest statistics from their 2021 Q4 report:
- 1030% increase in ransomware reports from Q3
- $6.6 million in direct financial loss was reported in Q4. 100% increase from Q3
- 568 scams and frauds, up 16% from Q3
- Recent DDoS attack on VOCUS, Kiwi Bank and ANZ
If you are unsure about what your business is doing in the cyber security arena, we recommend going through the list below and speaking to your IT Partner or your internal IT delegate to discuss and ask any questions you may have.
At the end of the day, prevention is key.
15 Ways to Protect Your Company From Cyber Attacks
1. Perform a Cyber Security Audit
The first step in protecting your business from cyber-attacks is to identify your company’s vulnerabilities. This can be done through a cyber security audit, which will help you to assess your current security posture and identify any areas that need improvement.
This assessment need not be too cumbersome.
It can be as simple as asking questions about your business’ password policy, what your process looks like when employees are onboarded or leave the company, or what backups you have in place and how they are being implemented.
However, depending on your business size, cyber maturity, and appetite for risk, this could be at the scale of penetration testing and ‘white hacking’ in order to make sure your network is robust and able to prevent external threats.
Why Is This Important?
By understanding your weaknesses, you can take steps to mitigate the risks and make it more difficult for attackers to exploit your vulnerabilities.
Knowing where you are right now will help you determine your next steps.
What is great about audits is that they are a snapshot of your cyber security position at that point in time. If you do this periodically, for example, every 6 months, you can see your progress over time.
According to the latest statistics, 71% of businesses that have been targeted by cyber-attacks have less than 100 staff members; identifying that just because you are a small business, it doesn’t mean you are immune to cyber-attacks or that you can continuously put a cyber-security audit on the backburner.
2. Check Your Spam Filters
One of the most common ways cyber criminals gain access to businesses is through phishing emails.
Phishing is a type of email scam where criminals send fake emails that appear to be from a legitimate source in order to trick victims into clicking on a malicious link or attachment.
Once the victim clicks on the link or attachment, they are taken to a malicious website, or their computer is infected with malware.
To protect your business from phishing attacks, it is important to have strong spam filters in place to block these types of emails from reaching your inbox.
Why Is This Important?
According to the CERT NZ report, phishing and credential harvesting was the #2 cyber security threat for the quarter. In past reports, this was often #1, indicating just how big this threat really is.
3. Update Your Passwords
Another way to protect your business from cyber-attacks is to make sure all your passwords are strong and up to date.
According to CERT NZ, only 41% of Kiwis say they always make sure their passwords are distinct, long, and complex when signing up to new websites or online services.
A strong password is one that is at least 8 characters long and includes a mix of upper and lowercase letters, numbers, and special characters.
You should also avoid using easily guessed words like ‘password’ or ‘123456’.
Why Is This Important?
If a cybercriminal gains access to your business’ email account, they will be able to reset the password for any other accounts that use the same password.
This is why it’s so important to have strong and unique passwords for all your accounts.
It is also recommended to use a password manager. This is a tool that helps you generate and store strong passwords.
A tip we often share is to stop thinking of passwords, rather, think of it as a passphrase.
For example: BananaMouseChocolateTree.
Want to see how long cyber criminals can “brute force” your accounts?
Try entering a few of your passwords here.
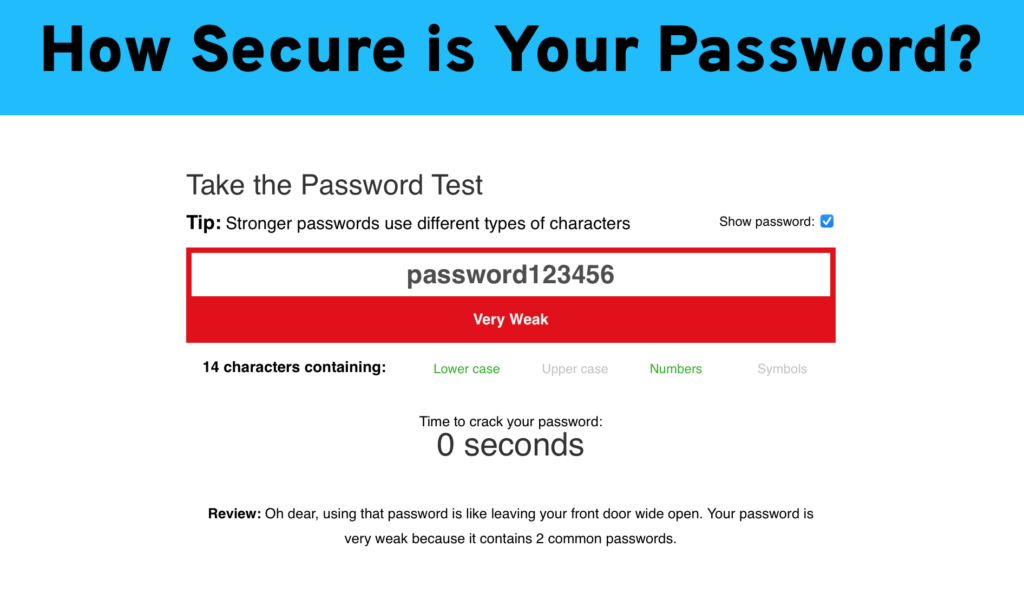
4. Conduct Continuous and Frequent Cyber Security Awareness Training
One of the best ways to protect your business from cyber-attacks is to educate your employees about cyber security.
While you can implement multiple layers of technology to protect your business, there is one component that you cannot neglect; that of human intervention.
Let’s say your spam filter (#2 above) caught a phishing email.
If your staff happens to still “approve” or click on these links, they can get hacked, making vulnerable sensitive business data.
Cyber security awareness training is important because it helps employees understand how to identify and avoid common cyber threats, such as phishing emails, social engineering attacks, and malware.
Why Is This Important?
According to an IBM report, “Human error was a major contributing cause in 95% of all breaches.” This means that even with the best security measures in place, your business is still at risk if your employees are not trained on a regular basis in best practice cyber security.
As a company, do you include cyber security training courses for new and current staff members?
Do you run phishing simulations?
From a business standpoint, cyber security training is also something we are seeing an increasing demand for, often pushed by insurance requirements.
5. Implement Advanced Endpoint Detection and Response
Endpoint detection and response (EDR) is a type of security software that helps businesses detect, investigate, and respond to cyber threats.
Unlike traditional antivirus software, which only looks for known malware, EDR uses behavioural analytics to identify suspicious activity and potential threats.
Why Is This Important?
Think of EDR as the next evolution of the anti-virus.
EDR agents protect against file-less and script-based threats and can even rollback a ransomware attack. It can detect attacks that have gone unnoticed.
The significant difference between EDR and your standard security software is that the former is more proactive, while the latter is reactive.
We recommend implementing an EDR solution if you haven’t already. If you need help choosing the right one for your business, get in touch with us and we can guide you.
6. Implement Multi-Factor Authentication
Multi-factor authentication (MFA) is an authentication method that requires two or more verification factors to login.
The most common type of MFA is two-factor authentication (2FA), which combines something you know (for example, a password) with something you have (for example, a smartphone).
Why Is This Important?
MFA adds an extra layer of security to your accounts and makes it more difficult for cyber criminals to gain access. For example, even if a cybercriminal knows your password, they will still need your phone to login.
We recommend implementing MFA on all your business accounts, especially those that contain sensitive data.
We understand MFA adds time when you’re logging in, but the unfortunate reality is, this is a necessary security step in today’s world that’s plagued by cybercriminals doing everything they can to get hold of your data.
Craig Hudson, Managing Director of Xero
7. Have a Patch Management Policy in Place
Patch management is the process of identifying, testing, and deploying software updates (aka patches). Regular patch management fixes vulnerabilities on your software and applications that are susceptible to cyber-attacks.
Think – servers, desktops, laptops, switches, phone, routers, etc.
When it comes to patching, you need to strike a balance between security and productivity. You don’t want to be constantly patching systems and disrupting workflows, but you also don’t want to wait too long and leave your business exposed.
The key is to have a patch management policy in place that everyone understands and follows. This should include a schedule for when patches will be deployed and who is responsible for testing and deploying them.
Why Is This Important?
One of the most common ways cyber criminals gain access to systems is by exploiting vulnerabilities in software. By patching these vulnerabilities, you can close the door on potential attacks.
Another reason you need to implement patch management is for compliance. This is becoming more necessary to adhere to internal standards and for insurance purposes.
Lastly, updates usually come with feature improvements and reliability. In essence, you increase the benefits you get while reducing your risks by implementing a patch management policy.
8. Consider Dark Web Research
The dark web is a place where cyber criminals buy and sell stolen data, malware, and other illegal goods and services. It’s also where they share information about new exploits and ways to conduct cyber-attacks.
Often when an organization like LinkedIn or Canva gets hacked, credentials (usernames / passwords) get sold on the Dark Web for phishing purposes.
Their hope is that the password ‘Ted’ uses for Canva is the same password he uses for his Microsoft 365. Now just imagine if ‘Ted’ also uses that same password for his banking and social media!
The resulting damage has huge ramifications.
Why Is This Important?
Regular dark web research can help you stay ahead of the curve and protect your business from potential cyber-attacks.
For example, if you discover that employee credentials have been compromised in a data breach, you can take steps to prevent them from being used to login to your systems.
If you do find that your data has been compromised, you can take steps to mitigate the risks.
Start by talking to your IT provider about this.
Oftentimes, they have tools available to find leaks. These services monitor the dark web for stolen data and notify you if your business is at risk.
9. Use Firewalls
A firewall is a network security system that controls the traffic allowed into and out of your network. It is a critical component of your cyber security strategy as it can help block malicious traffic and protect your data.
There are two main types of firewalls: hardware and software.
Hardware firewalls are physical devices that sit between your network and the internet.
They are usually used by larger businesses as they can be more expensive and require more maintenance.
Software firewalls are programs that run on your servers or workstations. They are less expensive and easier to maintain but cannot provide the same level of protection as hardware firewalls.
Why Is This Important?
Firewalls are important because they can help prevent cyber-attacks by filtering out malicious traffic. They can also be used to segment your network so that if one part of it is compromised, the rest of your network remains secure.
The firewall we recommend is the Unified Threat Management (UTM) Firewall.
The main difference between the UTM and regular firewalls is that UTM firewalls have services layered on top of it.
This is even more important today as you have remote workers coming onto your network and accessing your business data.
Inside your office building, this is not as much of an issue.
But when you have staff accessing your network from their homes (which usually have a less secure network) or at a nearby café, your risk level increases dramatically.
10. Double Check Your Web Gateway Security
Your web gateway is the first line of defense against cyber-attacks. It is the gateway that controls traffic going in and out of your network.
Cloud based security detects web and email threats as they emerge on the internet and blocks them on your network within seconds – before they reach the user.
Implementing a secure web gateway as the first line of defense, removes SSL blind spots, provides visibility into web traffic, allows for URL filtering, and DNS (Domain Name System) firewalling.
Why Is This Important?
This is important because if your web gateway security is not up to date, you are at risk of cyber-attacks. Make sure to double check that your web gateway security is up to date and that you have the latest version of your security software.
If you don’t have one or don’t know the details, use this opportunity to start a discussion with your IT partner.
11. Don’t Forget Your Mobile Devices
Mobile devices are an increasingly popular target for cyber-attacks.
These cybercriminals are counting on you to neglect this piece of the puzzle. This is why a Mobile Device Management program is highly recommended for your business.
Mobile Device Management (MDM) is a type of security software that gives you control over the mobile devices used to access your corporate data. It allows you to remotely manage and monitor devices, set up security policies, and wipe data if a device is lost or stolen.
Why Is This Important?
This is important because mobile devices are often used to access corporate data. If these devices are lost or stolen, the data on them could be compromised.
With an MDM program in place, you can remotely wipe data from lost or stolen devices to help protect your company’s data.
In fact, according to a Symantec report, 1 in 36 mobile devices have high-risk apps installed. That means that if you have 100 employees, at least 2 of them have a high-risk app installed on their phone right now.
High-risk apps are those that violate one or more of the following:
- Share sensitive data without permission
- Have excessive privileges
- Are from an unknown developer
- Are outdated
Without a policy or a way to manage these mobile devices, especially if they are being used to access your network and important files, you are at elevated risk.
12. Implement SIEM/Log Management
SIEM (Security Information and Event Management) and Log Management are tools that help you collect, monitor, and analyze data from various areas of your network.
This data can be used to detect and investigate security incidents.
It uses big data engines to review all events and security logs from connected devices to protect you against advanced threats and to meet compliance requirements.
Why Is This Important?
Having greater visibility across your historical log data is invaluable. It consolidates logged data into one location and helps you understand how users are spending their time and what they are trying to access as well.
13. Implement Encryption
Encryption is a process of transforming readable data into an unreadable format. This ensures that only authorised people can read the data.
Encrypting files helps prevent tampering or un-authorised access while files are in transit and at rest.
There are two types of encryption:
- Symmetric-key encryption: Uses the same key to encrypt and decrypt data.
- Asymmetric-key encryption: Uses a different key to encrypt and decrypt data. The keys are generated together and are mathematically related. Typically, using this type of technology solves this for you.
These proven safe tools can be found, as examples, on HP laptops and connected to Microsoft’s 365 software.
Why Is This Important?
This is important because encryption helps protect your data from being accessed by un-authorised people. If your data is encrypted, even if it is intercepted, the person who intercepts it will not be able to read it.
As an example, think of this as sending a letter in an envelope via mail.
There is no encryption other than the letter being inside the envelope. Anyone can simply open the envelope and by doing so, access and read the letter.
But with encryption, you add a layer of protection so that even if someone gets access to that letter, they will not be able to understand it.
14. Create a Backup and Disaster Recovery Plan
A backup is a copy of your data that you can use to restore your files in the event that they are lost or corrupted. A disaster recovery plan is a plan that describes how you will recover from a disaster.
Your backup and disaster recovery plan should include the following:
- What data you need to backup
- How often you will back up your data
- Where you will store your backups
- How you will recover your data in the event of a disaster
Why Is This Important?
This is important because it helps ensure that you can recover from a disaster. If your data is lost or corrupted, you can use your backups to restore your files and resume business almost immediately.
We strongly recommend following this three-step plan:
- Backup local
- Backup to the cloud
- Test your backups often
Remember, replication is not a backup.
For example, you have your files in OneDrive. You can access them on your phone, tablet, desktop, laptop in your office, during your vacation or where-ever you may be working.
This is a replication of files, not a backup.
Talk to your IT provider to gain a better understanding of backups and how you can implement it securely for your business.
15. Get Cyber Insurance
Cyber insurance is insurance that covers losses resulting from cyber-attacks. It can help cover the cost of data breaches, cyber extortion, and other types of attacks.
At the end of the day, having multiple layers of protection can only reduce your risks. There is no 100% failsafe way to ensure that your systems or data will not be compromised. So, if all else fails, protect your income and business with cyber damage and recovery insurance policies.
Why Is This Important?
This is important because it can help reduce the financial impact of a cyber-attack. Cyber insurance can help cover the cost of restoring lost data, repairing damaged systems, and other expenses associated with an attack.
When choosing a cyber insurance policy, be sure to read the fine print and understand what is covered and what is not. Some policies only cover certain types of attacks or losses, so it is important to know what you are buying.
One thing we do know from talking to insurance brokers, it is getting more difficult to obtain cyber insurance without first making sure various practices (like the ones mentioned in this post) are implemented in your business.
Over to You
There are many ways that you can protect your company from cyber-attacks. Implementing these security related measures will help reduce your risk of being compromised.
Simply your cyber security should concentrate on the big 3.
Technology, Processes, and People.
Neglecting one of these will leave your business at elevated risk. But by taking a comprehensive approach, you can build a strong defense against cyber-attacks.
If you found this post helpful, please share it with your friends or colleagues.
Do you have any other tips to share? Feel free to leave a comment below.
If you need help with your cyber security, don’t hesitate to get in touch.


