We’ve talked a lot about cyber security here on our blog and our social media accounts.
Why? Because it’s really important.
Yet most business leaders still don’t put too much thought into how they can protect their business. Most of them still believe in cyber security myths like “we’re just a small business, we won’t be targeted.”
If you didn’t already know, the vast majority of cyber attacks aren’t targeted. Meaning, whether you’re a large corporation with thousands of employees or a small business with just one staff, you can still fall victim to a cyber attack.
Cyber criminals don’t discriminate!
Click on any of these to jump straight to that topic
Another excuse we often hear is “we don’t need it” or “we’ll deal with it when we get there.”
As you already know, this isn’t a very sound plan.
One of the most common cyber attacks is in the form of malware . All it takes is one person to open a link or download a file —whether intentional or accidental— for a cyber criminal to gain access to your network and devices. When that happens, all your files will be inaccessible.
How do you think you can do business if you lose access to all your data?
Interested now? Below are 10 tips you can follow to protect your your business.
10 Simple Ways to Protect Your Business Online
1. Enable multi-factor authentication
Usernames and passwords are a key target for hackers, and with good reason — your identity and data are your most valuable asset.
Last January 2019, the biggest data breach (yet) exposed over 1.2 billion email addresses. A few months after, one of the most well-known online graphics software also had a breach that impacted 137 million subscribers.
Strong and secure passwords go a long way, but passwords alone are not the most secure authentication mechanism. Watch this video of a lesser-knownhacking that could wind up getting unnoticed by you or anyone in your organization.
Here are some quick facts:
- 90% of data stolen by phishing are user credentials.
- 80-90% of passwords can be hacked in under 24 hours.
Multi-factor authentication (MFA) gives you an additional layer of security. If you have MFA enabled in your accounts, you will be required to use two or more independent credentials to prove your identity. Once you finish those extra steps, only then will you be able to access your account.
2. Strengthen your passwords
Passwords are ubiquitous in our daily lives. From email to social media to bank accounts — we all have passwords.
They are the first line of defense in protecting your identity and data. Sadly, far too often, they are also the only line of defense.
Let’s take a look at these statistics:
- 59% know a secure password is important, yet only 41% choose a password that is easy to remember.
- 91% understand the risk of reusing passwords, but 55% do it anyway.
If your device or service doesn’t support MFA, the next best option is making your password harder to crack.
This cyber security manual provides more information like using a mnemonic over numeric ones. To learn more, you can download the PDF by clicking on the link above.
One other way you can create a strong password that is virtually impossible for hackers to crack is to use a password manager.
Yes, it’s another service that forces you to create another account and remember another password. But, what if that’s the only password you need to remember for the rest of your life? Head on over here to watch this step-by-step tutorial of how to use one of the most popular password managers out there.
3. Use anti malware software
Without an anti-malware or antivirus software, your PC could be infected by malware within minutes of connecting to the internet.
If you don’t have one, get one.
Now.
There are a lot of anti malware software out there to choose from. There are free and paid ones. Of course, the free ones will have limited capabilities, but it’s still better than having zero protection for your devices.
If you’re running Windows 10, you can download this manual for instructions on how to make sure it is running and how to keep it running — as it is common for malware to first target security programs.
4. Keep your software up to date
More and more malware is created every day. They are getting more sophisticated and intelligent that they can bypass anti-malware software from time to time.
But the fact remains that the older your software, the less secure it is.
This is why the most common ways for manufacturers and brands to combat vulnerabilities is by releasing updates or patches. This applies to both operating systems (OS) like Windows or Mac, and all the applications running on your computer like internet browsers, office applications, etc.
Another important group of devices to highlight are the Internet of Things (IoT) devices you have at home. These are your routers, smart speakers, CCTV cameras, light bulbs, and media centers.
5. Secure your browser
The #1 way we connect to the internet is through an internet browser. We use it for checking email, browsing social media, and searching the web for answers.
That’s why it’s also the #1 target for hackers.
Attacks via browsers typically come by way of an accidental or intentional click on a link that launches malware.
Here are four quick tips to ensure you reduce your chances of a malware attack:
- Use a secure browser — A quick Google search of the topic reveals big names such as Firefox and Chrome as the most secured browser.
- Heed warnings — If the browser detects you are visiting a (potentially) malicious site, it often shows you a warning page first.
- Keep it current — As previously mentioned, updates provide fixes to bugs and vulnerabilities. Enable automatic browser updates so you don’t have to worry about this again.
- Restrict content and plugins — Many browsers allow for plugins or extensions. Consider reviewing them and limiting your usage to the ones that you trust.
6. Router security and private network
Anyone who connects to the interned does so through a router. This hardware device, either wired or wireless, allows communication between the internet and your local network (i.e. your computer and possibly other connected devices).
In a 2018 report, routers were cited as the most frequently exploited type of device in IoT attacks. Hackers can use malware in design flaws to hide their identity, steal bandwidth, turn your devices into botnet zombies —or worse. They can also take advantage of any unsecured devices.
Just like with your browsers, here are 4 tips you can do to secure your network at home or work:
- Secure your network using a non-default administrator password. Note that this is different from your Wi-Fi password. This is the access to the administrator settings of your router.
- Configure the highest encryption supported by your router. Going from the strongest to the weakest, these are as follows:
- WPA3
- WPA2
- WPA
- WEP
- Keep your firmware up to date. According to one study, 83% of routers have vulnerabilities. A router with the latest updates is much less likely to be infected by malware.
- Use a Virtual Private Network (VPN) to add another layer of protection to your identity and information.
7. Protect yourself on public Wi-Fi
Public Wi-Fi is everywhere — cafes, airports, shopping malls, and outdoor parks. They’re incredibly convenient.
And dangerous.
Because of the public nature of these connections, there’s a real chance someone could take advantage of unsecured traffic. Watch this video to understand one of the real threats from an unprotected Wi-Fi network.
The best way to reduce your risks on public Wi-Fi is to limit your activity. Don’t work on any “sensitive” documents and send them over the network. If you must, make sure you stick to encrypted sites and use a VPN.
8. Stop visual hackers
As the modern workplace continues to move outside traditional offices to remote and public spaces, the possibility of being “visually hacked” is more real than ever. It’s simple, effective, and often gets unnoticed until it is too late.
The best way to protect yourself is to be aware of your environment. Always assume that someone could look over your shoulder and see what’s on your screen.
You can also consider using privacy filters on your devices, but that would only work if they viewing at a certain angle. According to a research published by the Ponemon Institute:
- 91% visual hacking attempts were successful
- 68% of visual hacking attempts went unnoticed by the victim
- 52% of sensitive information was captured directly from device screens
9. Encrypt your data
Do you know where your files and data are stored in your computer or laptop?
The hard drive, or in more modern devices, the solid state drive (SSD).
But did you know that your computer’s hard drive is only held in place by a few screws? Once removed, your hard drive can be access on another device. And if you haven’t enabled encryption on your hard drive, anybody can easily access your data and other sensitive information.
Whether you’re using a Mac or Windows, make sure that it is encrypted. And take note, encryption of your hard drive is different from having a password on your device.
That password only opens your device by default. You still have to enable encryption yourself. For example, on a Mac, that would mean turning on the FileVault under the Security & Privacy setting.
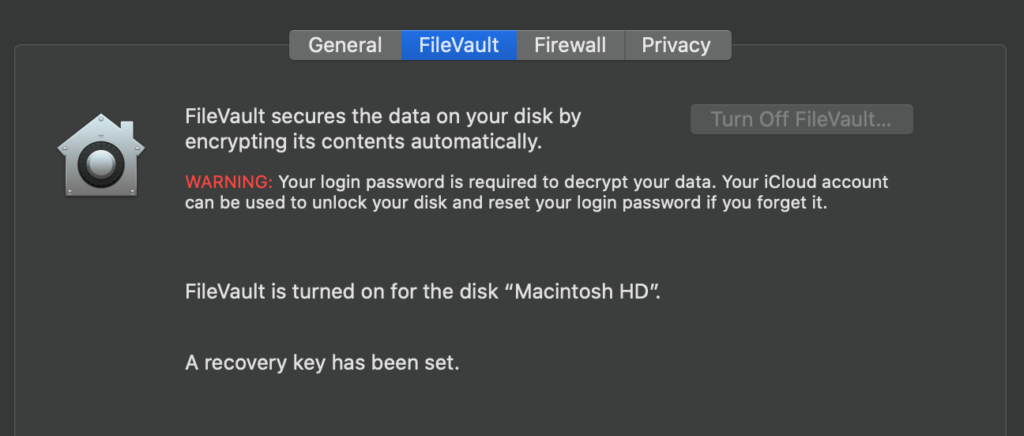
For Windows 10, there is a feature called BitLocker that provides software encryption that can be unlocked with a hardware key.
10. Secure your PC below the OS
The BIOS (basic input output software) is software that boots a computer and helps load the operating system. By infecting this core software, hackers can plant malware that remains live and undetected by antivirus.
If a hacker gains access to your BIOS, they essentially own every aspect of your PC. By keeping your software updated, any discovered vulnerability will have been fixed in the update. Another way to reduce your risk is to implement a BIOS password.
You can also limit unused features such as booting from external devices. Keeping this setting on can allow for malware to be loaded from external sources. If you really need to, that’s the only time you turn it on.
Over to You
Cyber security is a very important topic that business leaders like you should take seriously. The risks to your organisation is very real and very huge. More than 60% of businesses have shut down within 6 months after a successful cyber attack.
For specific steps on how you can protect your business from cyber attacks, download this free Cyber Security Field Manual.


