In the second quarter of 2022, cyber security incidents reported to CERT NZ decreased by 14%. However, this decline was overshadowed by a 5% increase in the financial loss caused by these incidents, reaching a total of $3.9 million.
One new threat that emerged during this period was phone scams, where attackers pretended to be from a bank in order to trick recipients into sharing their financial information or giving them access to their bank accounts.
This article provides an overview of the key findings from CERT NZ’s latest cyber security report for Q2 of 2022.
Related: When was your last cyber security audit?
Key findings in the 2022 Q2 CERT NZ’s Report
Total incidents declined by 14% from Q1 2022
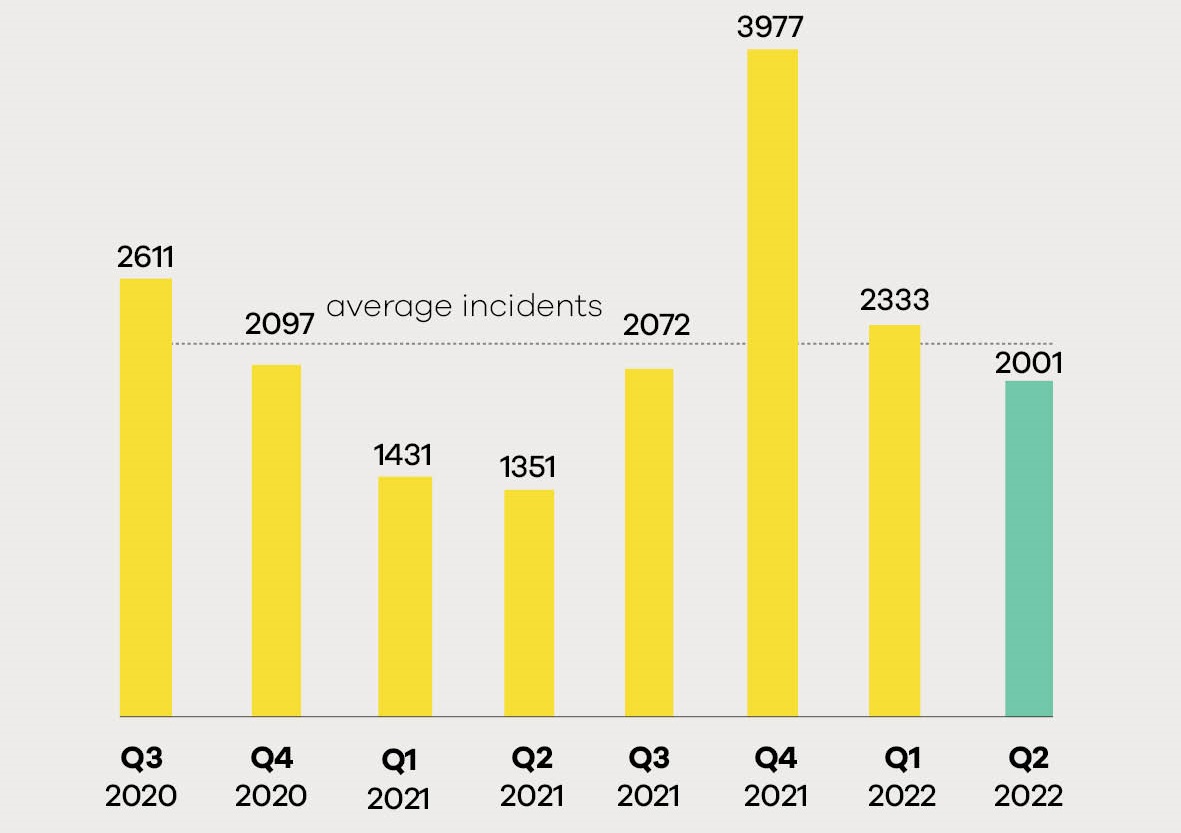
There were a total of 2001 cyber security incidents responded to by CERT NZ in Q2, which is a 14% decrease from the previous quarter but a 48% increase from Q2 of 2021. This indicates that the number of cyber security incidents is continuing to rise, and businesses and individuals must be increasingly vigilant in protecting their online information and resources.
Direct financial loss increased 5% up to $3.9m
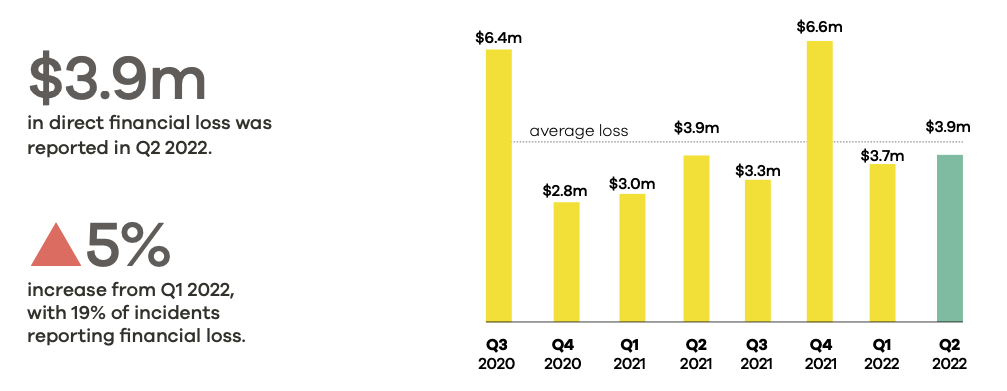
The total direct financial loss caused by cyber security incidents in Q2 was $3.9 million, which is a 5% increase from the previous quarter. This increase is likely due to financial scams discussed further below.
Indirect costs, such as the time and resources spent on rectifying the incident, were not included in this figure.
Breakdown by incident category vs Q1 2022
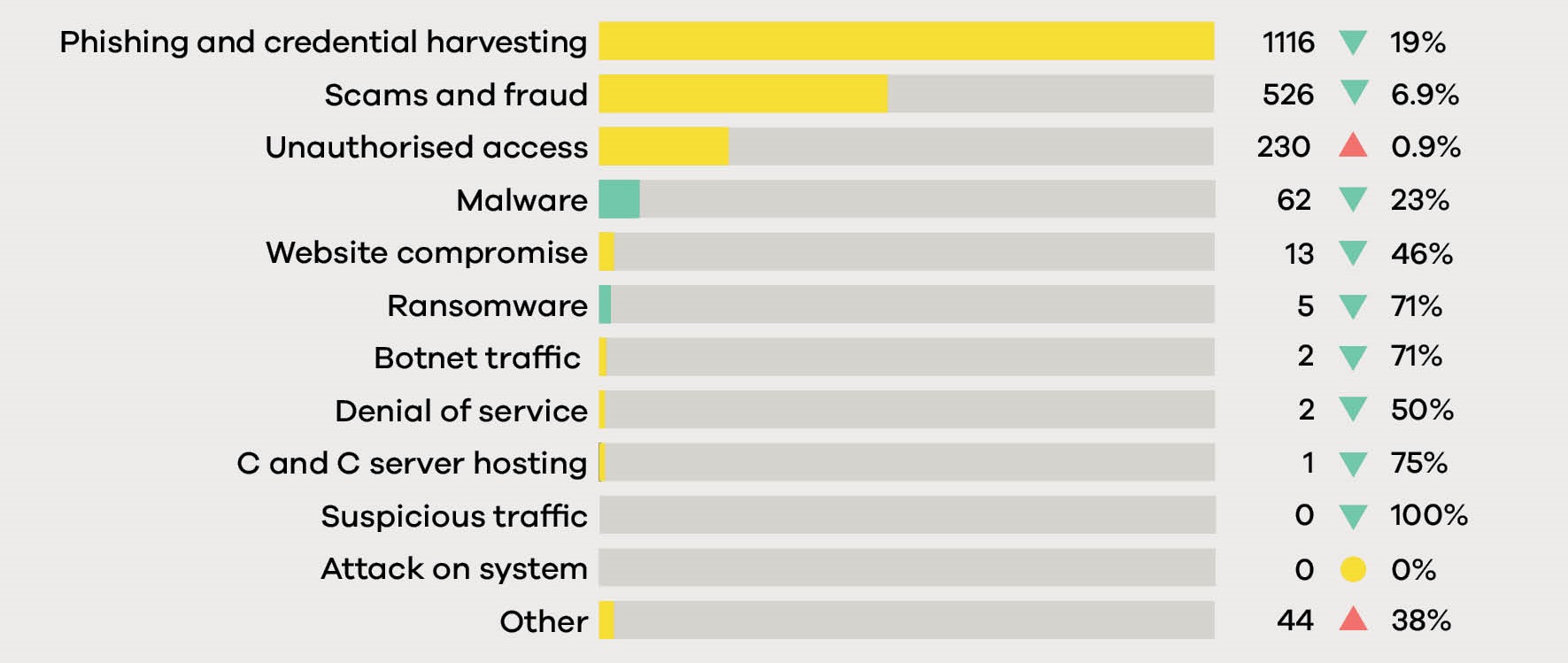
The most common type of incident reported to CERT NZ in Q2 was phishing and credential harvest (55%), followed by scams and frauds (26%). These two categories accounted for over 81% of all incidents reported. The next most common types of incidents were unauthorised access (11%) and malware (3%).
Beware of phone spoofing and scams
Phone spoofing is a technique used to change the appearance of a phone number when making a call. This can be done by using software that changes the caller ID, or by manipulating the signal on the phone line. Phone spoofing can be used to make it look like a call is coming from a different number, or to disguise the caller’s identity.
Scammers often use phone spoofing to make it seem like they are calling from a bank or other legitimate organization. They use social engineering tactics to try and get the financial information or access they are seeking. In many cases, they pretend to be from a bank’s fraud centre and say they’ve detected unauthorised access of the recipient’s account.
How CERT NZ is helping fight phone spoofing
In June, CERT NZ, New Zealand banks, and the Department of Internal Affairs (DIA) issued a media statement to warn the public about these fraud calls.
CERT NZ also provides relevant information regarding scam calls to the Telecommunication Forum (TCF), so they can analyze them and the scammers cannot utilize those phone numbers again.
What should you do if you receive a scam call
If you receive a suspicious call, hang up and call your bank or the organization the caller claimed to be from using their official phone number (do not use the number the caller provided).
You can find this phone number on the organisation’s website or at the back of your debit or credit card.
You can also report the incident to CERT NZ.
Don’t fall for romance and dating scams
Romance scams are a type of scam where the scammer takes advantage of someone looking for a relationship online. The scammer will use dating websites and apps or social media to build a relationship with someone. Once they’ve gained the person’s trust, the scammer will start to ask for money, gifts, personal details or they will make unusual requests that can be used to commit fraud or exploit the individual.
More recently, CERT NZ has seen reports where romance scammers are building trust to try and trick the individual to buy into crypto investment scams. The scammers often use fake profiles to make it harder to track them down.
How to protect yourself from romance scams
- Don’t give out too much personal information online
- A “reverse image search” can help you discover where else an image has been used, or confirm the identity of someone online.
- Do not respond to requests for financial assistance or make investments.
- Keep an eye out for varied communication styles. Multiple scammers may collaborate at times.
- Ask to meet up in person (in a public place) or do a video call. If the contact is unwilling to speak with you in person or by video conference, or offers a string of excuses to avoid doing so, they could be a fraud.
Prevent unauthorised access
As this quarter’s report shows, unauthorised access continues to be a prevalent issue, with 230 reports received.
An unauthorised access occurs when an attacker manages to get into a device, account or service without permission. This can be done by exploiting vulnerabilities in software, or by using weak or stolen credentials.
Once they have infiltrated a device or account, they can deploy ransomware, steal data and money, and cause other costly and time-consuming damage. It is essential to be aware of these threats and take steps to protect yourself and your organisation from them.
Why this is important for businesses as well as individuals
For individuals and their home, NAS devices and IoT devices are the typical targets. For businesses, Remote Desktop Protocol (RDP), websites and databases are some of the most commonly attacked internet-exposed services.
Since these are more technical than others, we recommend checking with your IT partner about your risks. Cybercriminals are always adapting their tactics, so it is important to keep up to date with the latest threats and how to protect yourself.
Stay vigilant
As the CERT NZ Cyber Security Insights Report for 2022 Q2 shows, unauthorised access and scams are on the rise, with cybercriminals becoming more sophisticated in their tactics. This is why businesses should not wait until they become a victim of cybercrime before taking their IT seriously.
If your business is not currently taking steps to protect itself from cybercrime, now is the time to do so. Contact iT360 today for a cyber security assessment and we can help you put in place the necessary measures to protect your organisation from these threats.



