Protecting yourself on the internet is important now more than ever. With just a few weeks in 2019, there are already dozens of news on different kinds of cyber crimes — from data breaches, ransomware, theft, and many more. And don’t expect these things to stop anytime soon.
As we rely more on the internet on a daily basis, it’s paramount that we know how to protect ourselves from people who are looking to exploit others.
If you care about protecting your privacy and other sensitive information, this article is for you.
Relying on Technology Alone Isn’t Enough to Protect You Online
First thing’s first, let’s define what technology means.
To keep things simple, technology means both hardware (physical products) and software.
Remember, no piece of technology will be 100% perfect. All of these are made by humans that’s why they cannot be without fault.
Example 1: When Hardware Fails
Home and business routers get slammed on a regular basis for exploits that get discovered. Because routers are not patched (or even secure, they keep the default username and password of Admin / Admin), they are vulnerable to hacks. Home routers more than business routers, but both if they are not constantly patched and checked.
Below is a screenshot from one of our engineer’s home network. Take note that he does have his own business-grade firewall at home which is more secure. It also gives reports on what’s happening behind the scenes (i.e. someone trying to hack your router).
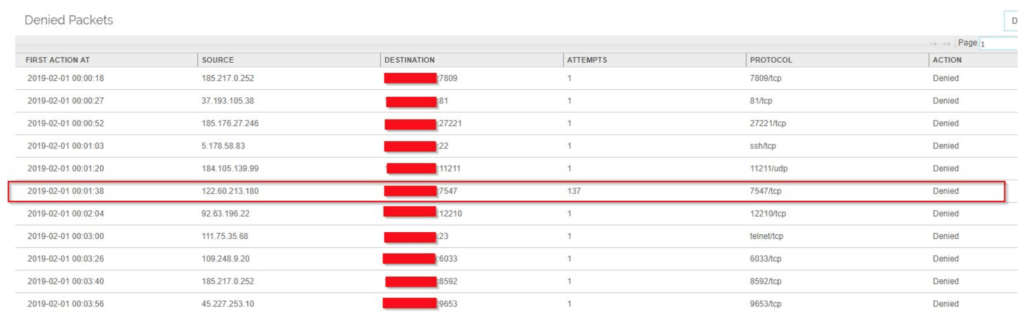
As you can see in the highlighted example, port 7547 was tried over 137 times which is this exploit.
You will also notice other ports that were tried within a time span of 4 minutes.
The sad part to this is that my ISP (which normally provides your home or default business router) doesn’t assist me in preventing any of these attacks. Even reporting back to them and giving them my logs, nothing is done. They do not feature in the security side of it all, so if you as the home or business owner don’t secure yourself – no one will.
Pieter van Zyl
Example 2: When Software Fails
A common example where software fails us is on email. Just take a look at your junk/spam folder. Our email provider’s spam filters catch most of these emails, but sometimes some come through our inboxes.
And if you aren’t aware of these phishing scams, you might accidentally install some malware on your computer, or fill-out a form with your information (like username/password).
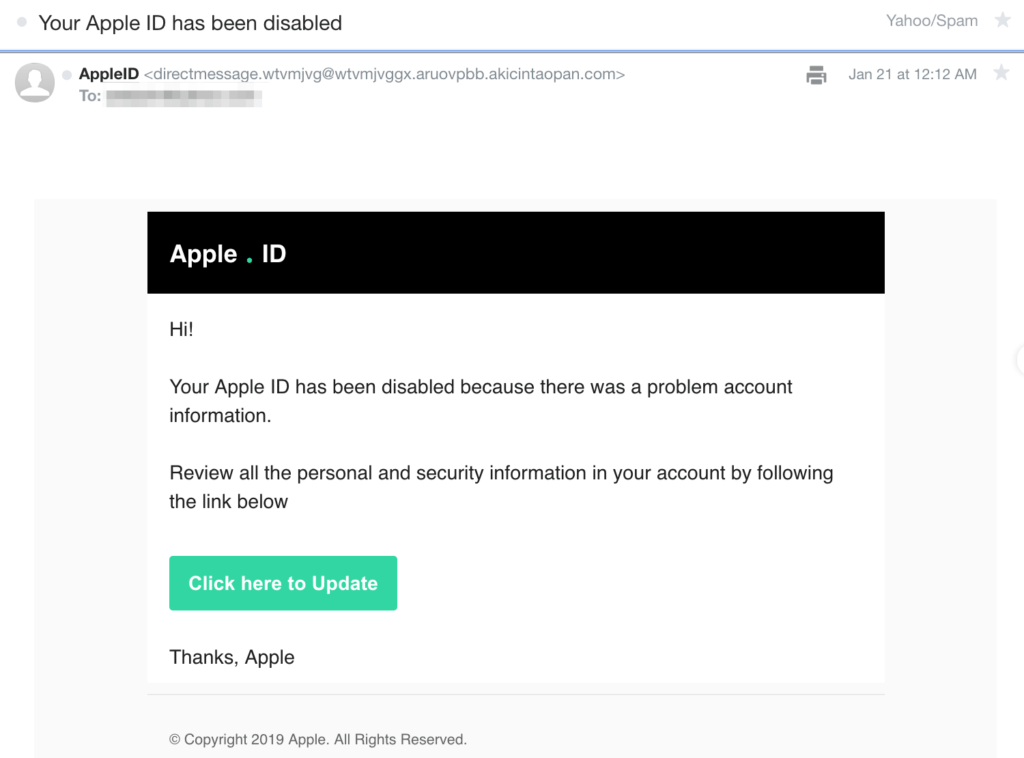
You’re the Last Line of Defense
When technology fails to protect us, the last line of defence against cyber criminals is yourself.
Remember the saying, “if there’s a will, there’s a way”? What that means is these cyber criminals are constantly trying to find ways to navigate around known security protocols to get your information and private data.
If you see an email in your inbox like the one above, what would you do?
Would you panic, click on the link, and enter your credentials? Or would you simply ignore it and mark the email as spam/junk?
When Ignorance Isn’t Bliss
We’re a huge advocate of multi-factor authentication (MFA). Basically, after entering your password, you get asked for a code to enter.
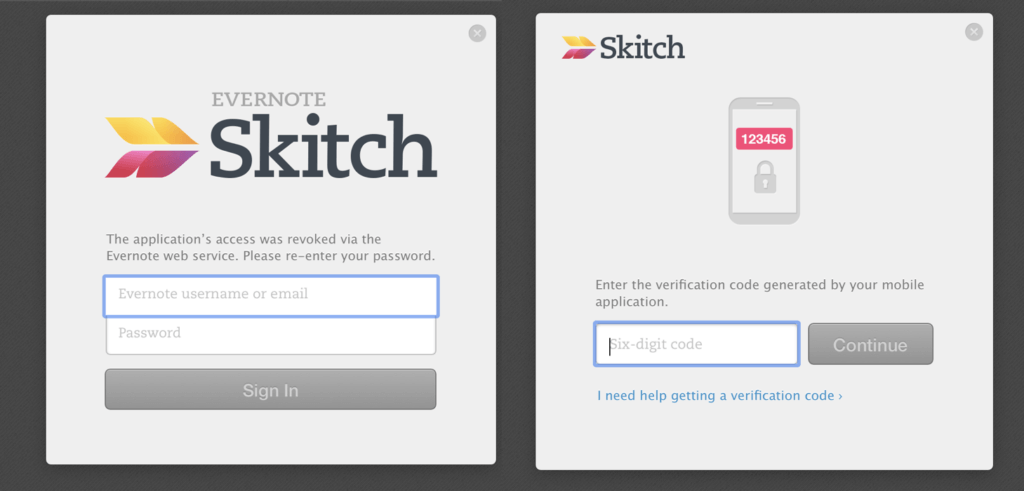
The example above uses an app to generate the code required in the right-hand image. There’s another type where an SMS is sent to your mobile number and that’s what you use instead.
But, did you know that two-factor authentication (2FA) via SMS is not as secure as you think?
Polish researcher Piotr Duszyński just published a program named Modlishka on GitHub where a hacker can potentially gain access to your account despite having 2FA enabled?
When asked why the programmer made the program public, his answer might surprise you.
“We have to face the fact that without a working proof of concept, that really proves the point, the risk is treated as theoretical, and no real measures are taken to address it properly,” he said. “This status quo, and lack of awareness about the risk, is a perfect situation for malicious actors that will happily exploit it.”
Piotr Duszyński
Awareness and Continuous Education Is the Answer
In cases where technology fails us, you’re the only one who can prevent your data and other sensitive information from getting stolen.
Read up on common cyber security threats that you may face in your daily lives. Here’s a list of the most common ones:
- IP theft — when individuals/organizations steal your ideas then launch products/services before you do
- Phishing — this is where you receive an email that asks you to go to a link, download and install something, or fill-up a form. Also, remember that this isn’t limited to email. It can happen via SMS, a tweet, or any communication channel.
- Denial of service — where you can’t access your website/server
- Ransomware — locking a computer system until a ransom is paid
Or the easiest way to stay updated on these things is to enrol in our special email series where we discuss these topics and how you can protect yourself online.
The first one we released is on the topic of passwords. If you want to learn more about using passwords in all your accounts — email, social media, work and productivity apps — to avoid getting hacked, just head on over here.



1 thought on “Protect Yourself Online by Focusing on These Two Things”