Let’s take a look at some disturbing facts:
- In 2016, 3 billion Yahoo accounts were hacked.
- Also in the same year, Uber reported that hackers stop information of over 57 million riders and drivers.
- The Equifax Breach in 2017 affected 147.9 million consumers
- Last year, 2018, Under Armor reported its My Fitness Pal was hacked, affecting 150 million users
- Two weeks ago, the Collection #1 data breach revealed the username and passwords of 770 million unique email addresses
These are all examples of cyber security breaches from big brands. If these numbers don’t scare you, it should. All of these numbers affect consumers and end-users like you. If you haven’t already, you should change your passwords right now.
Table of Contents
Now that that’s out of the way, here are a couple of tips to protect yourself and avoid getting hacked.
General Tips
1. Use a password/passcode on your devices
Now this might seem obvious, but a lot of people still don’t have passwords on their devices. If you’ve watched You on Netflix, you’d realize that Joe won’t be able to stalk Beth and know what she’s doing, where she is, and who she’s talking to if she used a passcode on her phone.
So, if you don’t have a password on your phone or laptop or tablet, go add one now. You’ll avoid a lot of headaches later on if you lose your device.
2. Don’t use the same password across your accounts
People have a tendency to forget stuff that doesn’t make sense to them. This is why we use simple passwords in our accounts, because they are easy to remember.
But this is also one of the reasons why you are at great risk of getting hacked. Take a look at this video of people getting interviewed.
Since we know that we can’t rely on our memory, we use that same password everywhere else. Imagine if someone got hold of your password — which you use in your email, social media accounts, and even your online banking. What would prevent them from using and abusing them?
The easiest way to remember this is to use a password manager like LastPass or 1Password. All your passwords are stored here, so you only need to remember one strong password — the password to your password manager. Then, to ensure that you add another layer of protection, use two-factor authentication (or multi-factor authentication).
3. Use multi-factor authentication (MFA) whenever possible
Wikipedia defines MFA as “a method of computer access control in which a user is only granted access after successfully presenting several separate pieces of evidence to an authentication mechanism – typically at least two of the following categories: knowledge (something they know); possession (something they have), and inherence (something they are).”
MFA is a way to ensure that not anyone can easily access your accounts.
An example of where you’re already using MFA is when you withdraw money from an ATM. You need your card (something you have) and your PIN (something you know).
But, most of the time, when it comes to our accounts online, we often only rely on our passwords (something we know). So, anyone who knows your password can gain access to any or all of your accounts.
How multi-factor authentication works:
Whenever you login to your account with MFA enabled, what happens is you go through the normal username/password routine. Once you enter your correct password, the account will ask for a set of code from you. Depending on how you set this up, you’ll either get an SMS with the code, or you use an app on your phone to get the code. You then have to enter this code within a few seconds; otherwise, you will need to regenerate another set of code. In some instances, you may also use an actual physical device that gives out the code (like what the app does).
When you use an app to get your code, that’s actually 3 layers of protection already.
- Password — something you know
- Phone — something you have
- PIN / access to unlock your phone — something you know (or have in the case of fingerprint or facial recognition)
This reduces the likelihood of your accounts being accessed by someone else. For example, someone tried to use the username/password combination that was revealed in the biggest data breach yet.
If you didn’t change your password, anyone could have easily gained access to your account. But if you have MFA enabled, you will receive an SMS, and you’d be notified immediately that someone tried to access your account.
4. Don’t click on any link/download files from people you don’t trust
We firmly believe that people are the last line of defense in protecting yourself from cyber criminals. Technology — both software and hardware — can only do so much. After all, ~47% of data breaches are caused by employees; while 96% of all data breaches, people have a minor contributor to the breach.
A lot of times, people with bad intentions can get passed the technology designed to keep us safe. The most prevalent case for this in via email. Someone sends you an email with a link to a website or a file to download.
If you do not know the person or company who sent you that email, mark it directly as spam/junk mail or delete it right away.
5. Use an antivirus software regardless of your device (Mac users, I’m talking to you)
As mentioned above, technology is your friend. You don’t have to fear it. And one of the most important software you need to have installed on your devices is an antivirus software. If you’re using Windows, most computers now come with one — Windows Defender.
But if you’re on Linux or Mac, this is usually something you need to install yourself. There are a lot of free ones out there to get you started. So, before moving to the next tip, I suggest you download one to your device and run a full system scan.
Most Mac users still believe that their system is immune to malware, but that can be further from the truth. While Mac devices often don’t get affected directly by viruses, their device can host these malware, which then can spread to other devices.
For example, you connect a USB device on your infected Mac then use that on your work computer (which runs on Windows). You might think you’re safe since your Mac isn’t affected. But that single act could have planted some sort of malware into your work computer and can affect everyone in the organization.
Related article: 15 Cyber Security Myths Business Owners Should Leave Behind in 2018
6. Upgrade your software/firmware when possible
Most modern devices have software that makes it run. At home, these would be your phones, computers, routers, and other smart devices you might have — speakers like Alexa, Google Home, or the HomePod; bulbs, outlets, thermostat, and even your garage door.
Whenever updates are made available by the manufacturer of your device, it’s best to upgrade your devices as well. Yes, it’s a hassle especially if there are multiple steps you need to do. Most of the time, these are security updates that reduces vulnerabilities in the previous version of the software.
A lot of modern devices have an automatic update feature enabled. Your laptop or your phones might have these enabled. But some of the hardware at your home might not support this. For example, your home router might be one of them.
When connecting to the internet
7. Use a VPN
Using a virtual private network (VPN) provides you a lot of benefits, but the most noteworthy among them are these two: enhanced security and anonymous browsing.
Let’s say you use the internet on your computer. VPNs provide you additional security by encrypting your data before it gets sent to your router. That means no one can see the information — usernames, passwords, emails, documents, etc.
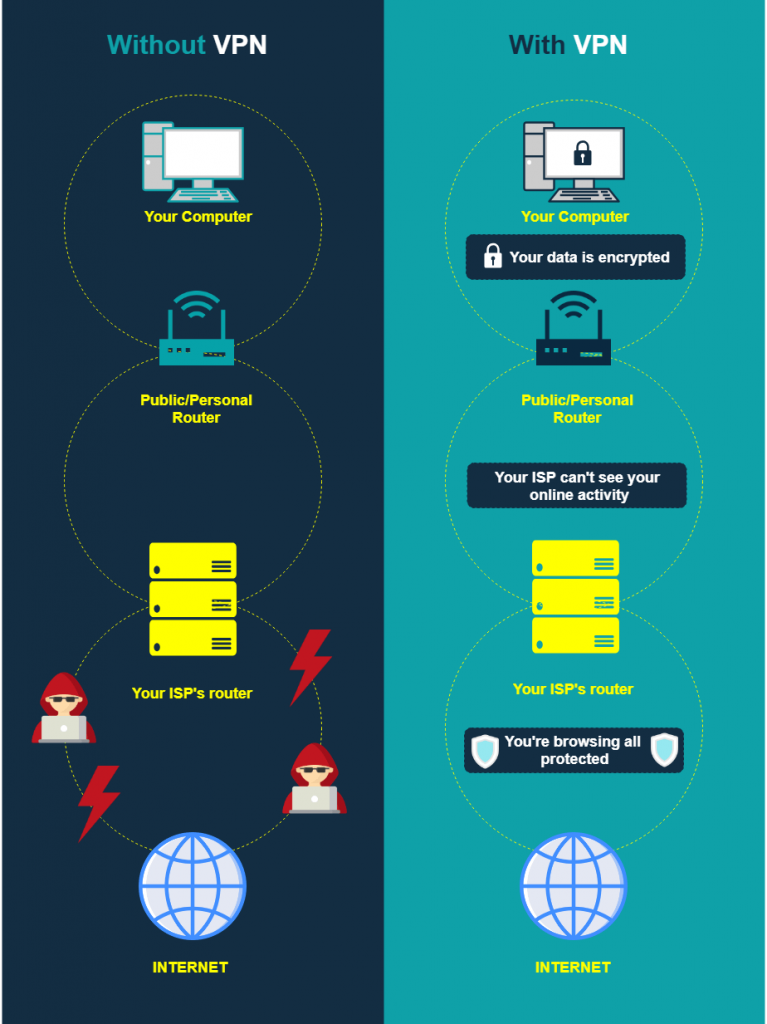
Then, what happens is your router connects to your internet service provider (ISP). The second benefit kicks in here since the ISP can’t know what you do. There’s actually a second layer of benefit with anonymous browsing — you can get pass geo-restrictions.
We’ll talk about that some other time. But what that means is, let’s say you watch a lot of Netflix. There are some shows that are not available/restricted to the location of your ISP. VPNs allow you to use a different IP address so it looks like you’re at, for example London, when you’re really in Auckland.
8. Always logout of your accounts if you’re sharing your computer/public computer
In cases where you need to access your accounts at a public computer, remember to always sign out afterwards.
9. Permanently delete all files you downloaded in public computers
And if you downloaded something to that computer, don’t forget to delete it permanently as well. Remember, when you delete something, it puts the file in the recycle bin (Windows) or Trash (Mac).
- To delete a file permanently in Windows, select the file(s) then press shift + delete.
- To delete a file permanently in Mac, select the file(s) then press option + command + delete.
In both cases, you’ll be asked if you want to delete the file permanently. Go ahead and choose yes.
Of course, you can always go inside the recycle bin/trash and delete it there yourself, but that route takes longer because you have to search for the file first before you can delete it.

While traveling
When you’re traveling, especially to a different country, remember to follow the same guidelines as above. Below are a few additional tips to avoid getting your information stolen.
10. Avoid online banking
As much as possible, avoid logging in to your bank’s accounts. Make sure you bring enough cash with you so you don’t have to keep using your credit cards then end up having to check your transactions.
11. Connect only to trusted networks, if possible
If you absolutely must, only connect to networks that you trust. If you have data roaming, you can use that. This reduces your risk of anyone spying on what you do.
Of course, if you’re using a VPN already, then you don’t have to worry about any of this. Just make sure no one can view what you’re typing on your screen.
12. Use your own internet connection, like your phone’s data/pocket wifi vs a public wifi
If you don’t have data roaming, an option you might want to go for is get a pocket wi-fi so you can access the internet.
At home
One of the biggest mistakes you can do is to think that you are not at risk at home. While we hear big named brands in the news getting hacked or information stolen, you may not think that that affects you. But in reality, the data that gets stolen are information about consumers and end-users — that’s you.
So, the next time you get back home, follow these simple tips to protect yourself.
13. Use a strong password
While we mentioned passwords earlier, this one bears repeating.
Often, home wifi passwords use a person’s mobile phone number or birthday. While it’s relatively better than using the worst passwords of all time — “password” or “12345678” — it’s still not enough.
And while we’re on the topic of passwords, make sure you actually do have a password. We strongly recommend a unique password so people can’t just access your internet.
14. Upgrade your router’s firmware
Did you know that 83% of routers contain vulnerabilities?
In other words, you’re most likely using a router at home that can be easily hacked. If you have CCTVs or speakers connected to it, the hacker can easily watch and listen to you.
Just like any other technological device, your home router runs on some sort of software/firmware. Occasionally, manufacturers release an update that either makes your connection better or provide further security.
Whatever that reason is, if there’s a new update available, you should go ahead and install it.
15. Upgrade any IoT device (Google Home, Alexa, Home Pod, etc)
This falls under the same risks and concerns as upgrading your router. For every smart device, you give it permission to access your home router. If there are vulnerabilities in the device, hackers can get in your network and steal your information.
16. Change the credentials of your router’s admin section
Lastly, the most important thing you need to do at home is to change the credentials of your router’s admin settings. It’s the area where you can change your wifi password,
If you do a quick Google search, the most common username/password combinations your router is public. For example, Linksys routers usually have an “blank”/admin combination.
If you don’t change this, the least damaging thing that can happen to you is your neighbor can get access to your internet — for free. But if someone with malicious intent gets in your network, they can potentially steal your credit card information, copy your data, monitor your usage, watch you on your webcam, listen to you on your devices, and many more.
Buying something on the internet
Buying something on the internet is becoming one of the most common activity we do online. According to NZHerald, NZ spends $3.724b annually in online retail. So, it’s only fitting that we include specific tips for for Ecommerce.
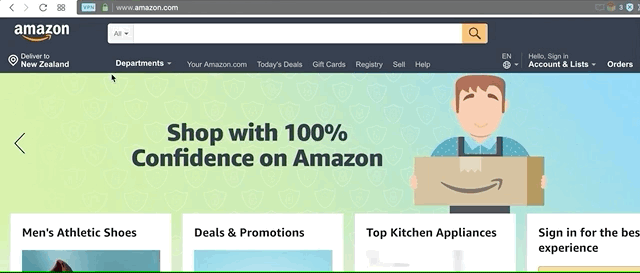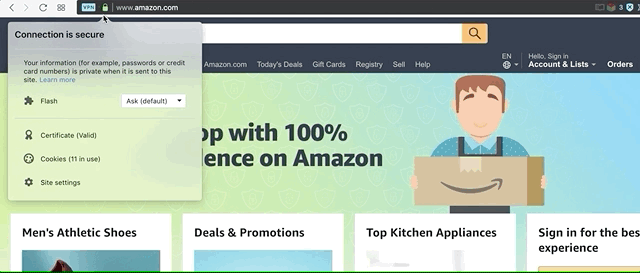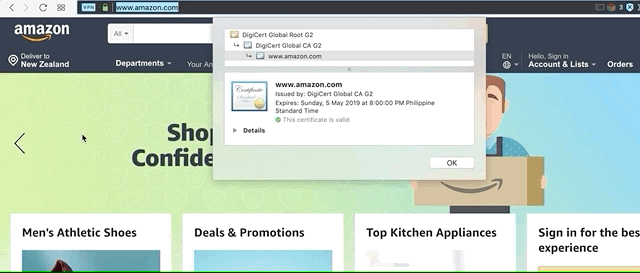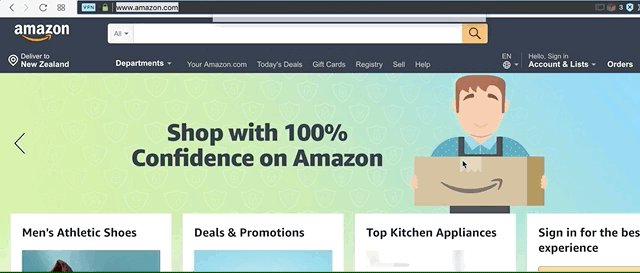
17. Look for the SSL icon (green lock icon at the top of your browser)
When you buy from a website, always look for the SSL icon at the top of your browser. SSL stands for Secure Sockets Layer.
There’s no need to go into the technical details of how SSL works. What matters is that SSL protects you by hiding(encrypting) the information you enter on your web browsers like credit card details and your address before it gets sent to the website itself.
18. Buy only from trusted sites
Even if a website has SSL installed (that green padlock), it can still lead to someone trying to steal your information. According to PhishLabs, a phishing research and defense firm, about 25% of phishing sites have SSL installed.
Continuing from above, if a site has SSL, anyone who might try to steal your information while being transmitted from your browser to the website won’t be able to.
But, if that data you entered goes directly to someone who plans to use it for their personal gain, then you still won’t be protected.
Remember, a green padlock indicating a site is secured doesn’t mean the person/brand behind it will respect and protect your privacy and data. So, only buy from trusted sites.
Using email
Email is still the most frequently used communication around the world. It’s also where majority of scams and viruses happen. Follow these tips to avoid getting hacked or scammed.
19. If someone asks you to wire some money to a certain account, run away the other direction
If anyone sends you an email asking for money, this should raise a red flag, especially if it’s someone you don’t know.
It’s one of the ways hackers trick people into sending them sensitive information or getting money directly.
20. If the email asks you to click on a link and asks for your username AND password, don’t do it.
Think about it. Why would a friend, a big corporation, or a family member ask you for your username and password? Unless you’re really helping out someone with their account, no one will ask you for these credentials. So, if you receive an email asking for these (or SMS, or from one of the hundreds of messaging apps out there), don’t do it.
21. Check if the person/company who sent the email is really who they are
If you think that email might actually come from someone you know or from an organization, there are a lot of ways to verify if the person requesting for information from you is someone you know or someone pretending to be them.
1. Click on their name to display their email address
Doing this will display their email address. If it looks something like sdgfhkbjsdkjfs@hotmail.com vs johnsmith@gmail.com, then it’s someone just trying to pretend to be them.
Don’t reply, nor engage with the email. Mark it as spam/junk, or delete it altogether.
Unless, of course, you know what you’re doing.
2. Open the browser URL directly, not click on the link
If it came from a brand/organization, it’s best to open a browser directly and type in the URL instead of clicking on the link.
If the link in the email is different from the one where you typed the address directly on your browser, then that email is most likely a scam. You can check the link in the email by hovering your mouse on it and the URL will be displayed.
Cyber security doesn’t have to be daunting. The more we rely on the internet, the more we have to protect ourselves from people who try to take advantage of others.
Don’t be a victim.
Follow these simple tips when using the internet, while travelling, at home, at work, and when using email.



1 thought on “Don’t Want to Get Hacked, Follow These 21 Cyber Security Tips”