If you have been avoiding cyber security because you think it’s not going to happen to you and our business, well, it’s time to find out if that’s exactly the case.
In this article, I’m going to show you a tool that can search the dark web for compromised email addresses and passwords in your entire organisation.
Now, there’s no more guessing about what-if scenarios and whether the risks of cyber security is real or not.
Interested? Read on…
The Dark Web
If you aren’t familiar, the dark web is a small part of the internet where illegal activities are conducted. In short, these is where hackers and criminals buy and sell information.
Your information.
Let that sink in for one second.
Your personal, identifiable information is sold/traded around by people without you knowing about it.
The why and how isn’t important at this point. But what matters to you as leaders in your organisation is to know which accounts have been compromised.
These data can be in the form of:
- email addresses and passwords — including where you use them: social media, bank accounts, email
- the address you live
- credit card numbers
Real Threats to Your Organisation
Example 1: Impersonating Your CEO
What if a cyber criminal gets hold of your CEO’s or president’s email.
The hacker can easily send an email to treasury to pay a certain bank account immediately; otherwise, a shipment will be blocked, or a lawsuit might happen which will inevitably cost more.
As the person in treasury receiving that email, what do you think he/she would do? Note that the email is valid — it came directly from the CEO or president.
There’s a variety of tactics used here namely social engineering (impersonating the CEO) and probably taking advantage of a data breach or lack of multi-factor authentication (MFA). Learn more about these common cyber security terms here.
Example 2: Knowing Your Every Move
If the previous example might sound unrealistic, how about this more subtle way of hacking. Watch this video…
The video describes multi-factor authentication (MFA) but presents a real-life scenario of a customer finding out that an email forwarding address has been set up in the account without their knowledge.
Now, imagine someone gaining access to all your emails and conversations? From your loved ones, your work, etc.
Now, that person would have known who you’re talking to, where you’re going, where you live, what projects you’re working on, and possibly the thoughts inside your head.
What do you think will happen if the project you’re working in is leaked to your competitors? What if someone posted sensitive
These are just a few examples of how serious the ramifications are and why you need to prioritize cyber security in your organization.
Want to Find Out the Compromised Accounts in Your Organisation?
At the beginning of this article, I told you about a tool that we use that searches for compromised email addresses and passwords.
Basically, the only thing you need to enter is your website.
What this tool does is search the dark web for the email addresses in your domain and compile them into a PDF report.
Here’s what it looks like with the email addresses and passwords masked.
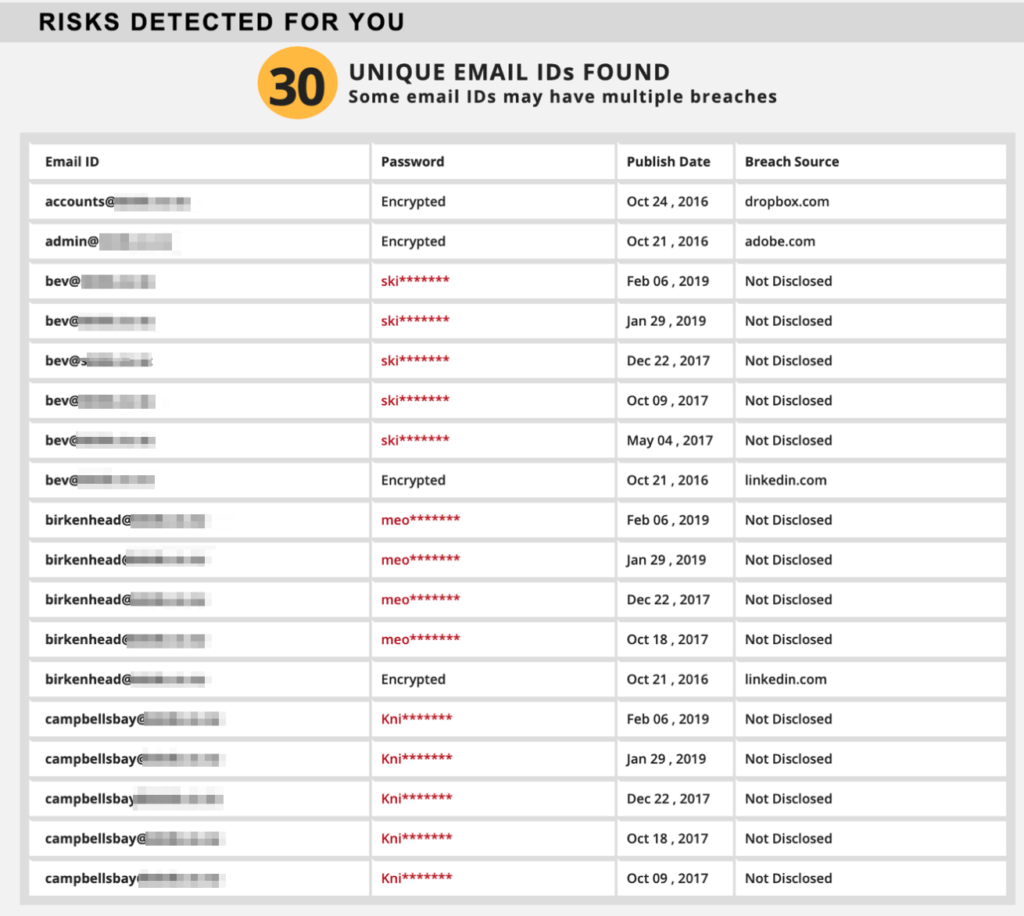
This report will display the email address, the password, when it was discovered/used in the dark web, and where it happened (source of breach).
For the purpose of this article, I masked/hid the emails and passwords. But, in the report that you’ll get from us, you will actually be able to see these passwords. This will give you specific, actionable steps on what to do in order to protect you and your business.
Why You Should Take Action Right Now
As I mentioned earlier, the implications of a breach is great. If your passwords are out there for everyone to see, there’s no telling what they’ll do with it.
Ok, you might tell yourself, “these are business email addresses, I’m pretty sure this won’t affect me personally.”
Think again.
At least 83% of people reuse their passwords across multiple services.
Just take a look at the password column of the image above. You’d notice that there are several instances of the same email address compromised with the same password.
Now, answer these questions:
- Do you reuse your passwords?
- How often do you change your passwords?
If you’re most people, you’re probably using the same password across the same set of services. For example, one password for all your online banking, and another for your social media accounts.
But even if you don’t reuse your passwords, or change them regularly, as leaders in your organisation you have to look at this from a bigger perspective.
The fact is most of the people in your organisation reuse their passwords. And that puts your entire business at risk.
83% of people reuse their passwords across multiple services
Cyclonis
Risks Extend to Your Personal Life
If someone gained access to your business email addresses and passwords, what do you think will happen in your personal life, given that you most probably use the same passwords there too?
Financial
Consider what would happen if someone can gain access to your online bank account? They can easily transfer money to certain accounts or use your information to impersonate you and steal something else.
Reputation
Or even worse, they can gain access to private information like getting access to your iCloud account and see your personal photos. These criminals can easily blackmail you to do illegal and shameful activities for them, or extort you for money.
Physical safety
What if these criminals found out where you live?
What do you think would happen to your spouse and your family?
Over to You
We’re on a mission to make the world we live in a safer place, one individual, one organisation at a time.
That’s why we want you and your organisation to get that peace of mind online. The report will give you specific and actionable items that will help everyone in your organisation to be safe.
If you want to learn more about this report, let us know in the comments below.
Fact is, over 70% of SMBs have been targeted by a cyber attack. And that’s probably even an understatement.
The latest study by the Ponemon Institute on behalf of IBM found that the average time required to identify a data breach is currently 197 days.
That’s more than 6 months. And that’s just the average.
If you don’t have the resources, processes, and tools setup, you might already been breached and don’t even know it yet.
Take this chance to put your mind at ease.


